When I ended part 2, I had a functioning router with a WAN interface and two subnets. But unless you only have a couple of clients to connect to the router, how are you going to turn that one interface into many? Hubs are stupid and broadcast everything. A switch is better because it limits collision domains. However, with two subnets, using just one switch is rather pointless as it would join them together. What is needed is a managed switch so we can set up VLANs and separate those networks. So that’s what I bought.
Managed switches can be pretty spendy, especially if you are going for brand names. I could have spent a few hundred dollars for a Cisco managed switch, but that seemed to be overkill. Instead, I went with a no-name Chinese brand called TP-Link for about half the price. The reviews were decent so I decided to give it a try.
A switch is a bit less complex than a router, so I didn’t have as much configuration as with the EdgeRouter. The GUI is pretty decent and the English translations passable. After configuring an IP and changing the default password (always do that first!), I was ready to tackle VLANs. At least I thought I was ready. VLAN tagging has a relatively simple interface, so I configured what looked right to me….and immediately crashed my network. Oops.
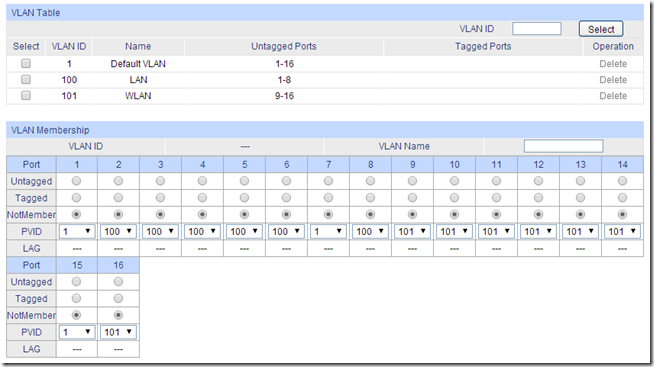
Fortunately, though, there were tutorials online as to how to configure these TP-Link switches to set up VLAN tagging. This one in particular was exactly what I was looking for. I set up VLANs 100 and 101 for my wired and wireless subnets respectively, and determine which ports I would essentially be trunking back to the router. I came up with this config:
The PVID represents what VLAN untagged traffic gets tagged with, so you can see that ports 2-6 & 8 are on the wired VLAN, and 9-14 & 16 are on the wireless. Ports 7 and 15 go to the router. Port 1 I kept untouched for local connectivity to the switch if necessary; I’m not comfortable enough with my networking skills to mess that one up, and too often my VLAN twiddling caused me to drop my connectivity to the switch, which made it rather hard to fix my screwups.
With this setup, my subnets are logically separated (I think!). Traffic from one must pass through the router, not just the switch, and be processed by my WLAN<—>LAN firewall rules (more on those later). I can lock things down very tightly with this configuration.
There is one thing missing: EdgeOS can do VLAN tagging too, and I have not extended these VLANs to the EdgeRouter (packets are untagged when they go through ports 7 and 15 connected to the router). Why haven’t I done this? Eh, no reason to do so yet, I guess. However, I would like to set up a separate guest wireless network, in which case I would definitely need to use the VLANs on the router since all of my interfaces are used up; I could, for example, put two VLANs on my WLAN interface. Doing that I could ensure that a guest wireless network would have no connectivity to my standard wireless, and I could again set up firewall rules to ensure that never the twain shall meet. A future project, perhaps.
At this point, I have a nicely-working network that I can now expand to several wired clients and several wireless access points to provide maximum signal coverage (and even guest wireless networks in the future). So, am I finished? Of course not! See, the ACL-based firewall rules are okay, but they are not granular enough: again, they only allow inbound, outbound, and local rules. Especially if I set up VLANs on the router, that will not do. So what’s the answer? Zone-based firewall rules! And that will be covered in the next edition.

1 comment
Comments are closed.