It’s been a while since I’ve done some Splunk work on my home network, but lately I’ve been thinking about port scans, specifically about reporting on port scans against my environment. I’m not terribly worried about people scanning my network since it is quite locked down, but why not check on it to see if anything interesting is going on? Before too long I had a new dashboard; details below the jump.
The last time I did this, I was trying to map brute force attempts. Port scans are similar, so I started with the search I did for the brute force attempts, tweaked it a bit with some help from the internets, and this is what I got:
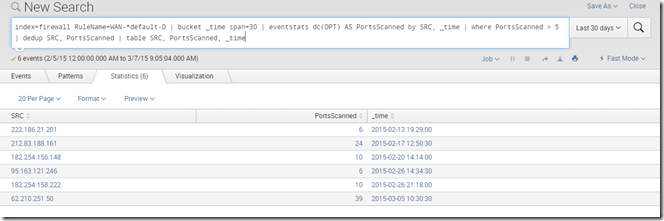
index=firewall RuleName=WAN-*default-D | bucket _time span=30 | eventstats dc(DPT) AS PortsScanned by SRC, _time | where PortsScanned > 5 | dedup SRC, PortsScanned | table SRC, PortsScanned, _time
Walking through this step by step: the first section says to search my firewall index, and to only include logs of rules that match WAN-*default-D, which is my rule nomenclature for traffic that originates from the WAN zone and is dropped by my default drop rule (meaning no pre-existing connection existed, it just came out of the blue). Then it buckets the time into 30 second buckets, since it could take several seconds to do a port scan of numerous ports. The eventstats command counts the number of distinct (dc) destination ports (DPT) that are scanned in each time bucket from the same source IP (SRC) and names that field PortsScanned. It then only includes results where the number of ports scanned is greater than 5: a single port is not a scan! Finally, it dedups the data and shows it in a nice table.
The result is this:
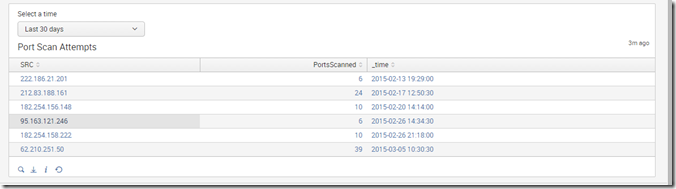
A little dashboard work, and now I have a dashboard panel that includes a way to quickly change the time span:
As before, I could easily map this with the iplocation and geostats functions. Quick and easy!